Abstract
The immediate disaster response environment exposes people to a multitude of risks, including identity risks. Those working in disaster response environments use identity management systems to protect people, especially vulnerable people and children. This paper examines identity management systems and the way they address risks of child trafficking and exploitation.
This research offers a unique perspective into the experiences of non-state actors and the role they play in identity management systems during disaster response. A case study of Tropical Cyclone Winston is used to explore views of identity management and how they reduce risks to children. The case study showed that the role of the community in identity management, verification and associated controls were geographically concentrated and not readily portable. This created risks to children of trafficking and exploitation, particularly where evacuation centres and shelters were geographically removed from the children’s communities.
An Event Analysis of Systemic Teamwork method revealed that those working in the disaster response environment rely heavily on information from the community and government when identifying children. Where there are gaps in the information and social networks in the identity management process there are significant risks to children. These insights are relevant to disaster response planning.
Introduction
Children are vulnerable members of society and their risk of being affected by natural disasters is higher than other members of the population. The inherent chaotic and complex nature of a disaster response environment (DRE) includes the breakdown of normal protections, including law enforcement and regulations. In these environments, children are at an increased risk of being trafficked and exploited and require increased protection (Harper 2009).
The connection between the risks of child trafficking and exploitation and the adequacy of identity management systems and related controls is not new. In 2011, the United Nations (UN) Special Rapporteur on the sale of children, child prostitution and child pornography, Ms. Najat Maalla M’jid, found that the data for unaccompanied children was inadequate and the exact risk of vulnerability was unknown (M‘jid 2011).
Save the Children (2007) found that children in developing countries are disproportionally affected by natural disasters because child protection is not integrated as a priority. DREs are characterised by actor interdependencies, individual and common agendas and are overlaid with environmental uncertainty where existing systems are damaged or non-existent (Harper 2009, p. 15; European Commission 2013, p. 7; Save the Children 2010, p. 26; Anaya-Arenas, Renaud & Ruiz 2014, p 55, 66). M’jid’s (2011) findings suggests there is lack of knowledge and experience in identification and registration processes among first responders and this increased the risks to children. These findings indicate the need to understand identity management systems and, where risks occur, the exposure of children to exploitation and trafficking.
Vulnerable people and exploitation risks
The literature on vulnerable people and the increased risk of exploitation and trafficking is extensive from a practical perspective, but limited from an academic perspective. The Inter-Organisational Protection Assessment of Tropical Cyclone Winston recognised that security risks including family violence, sexual violence, missing persons and children and child abuse increase during a disaster (Safety and Protection Cluster 2016, p. 10). The most vulnerable to these risks are young and adolescent girls, female-headed households, boys and adults with disabilities (Lonigan et al. 1994, Shannon et al. 1994, Vogel & Vernberg 1993, Safety and Protection Cluster 2016).
There are few academic studies that connect the three concepts of trafficking, exploitation and identity management systems in DREs. Research efforts draw the connection between trafficking and exploitation, geographical dislocation and travelling alone. One-third of child trafficking victims are unaccompanied or separated children (Bump & Duncan 2002). Unaccompanied minors travelling without identity documents are at risk of being trafficked during the reunification process with parents, guardians or caregivers (Derluyn et al. 2010). The risks arise when the parent, guardian or caregiver’s identity is not checked, or checked by staff with inadequate training in recognising false identity documents (Derluyn et al. 2010).
The 2010 Haitian earthquake provided press articles on child trafficking post-disaster. The complexity of stakeholders, specifically non-government organisations (NGOs) not accountable to a higher body or system, were a high risk to children. Article 27 of the UN Convention on the Rights of the Child, states that it is the responsibility of the State to protect its children. However, increasingly, the role has shifted to non-state actors (UN General Assembly 1989). The large volume of NGOs indicate that communication and consensus is difficult; 400 NGOs were present after the Indian Ocean 2004 tsunami (Tatham & Houghton 2011). Contemporary natural disasters with Australian involvement include Hurricane Yolonda (Philippines) and Tropical Cyclone Winston (Fiji). In both examples the literature highlights the safety of children and vulnerable persons as an area of concern (Oxfam International & Aksyon Klima Pilipinas 2013, Lum & Margesson 2014, European Commission 2013, OCHA 2016a, OCHA 2016b, Safety and Protection Cluster 2016).

Children are reunited with their grandmother for evacuation from Port-Au-Prince, Haiti following the earthquake in 2010. Image: US Air Force
Methodology
A mixed-method, multi-disciplinary approach was used to analyse the identity management system present following Cyclone Winston and its effects on children. The data are qualitative and collected in the form of Critical Decision Method (CDM) interviews with experts who worked in the Tropical Cyclone Winston (Fiji) DRE in February 2016. CDM is a method that extracts critical decision-related information in human factors research (Klein, Calderwood & Macgregor 1989). CDM allowed the examination of specific identity and child protection processes, dependencies and decisions, timelines, actors, information exchange, processes and tasks. CDM offered a data collection method that afforded naturalistic environment extraction through key actor recounts of decision-making and observations. The interview data are supported by qualitative data in the form of primary and secondary reporting including operational reports.
The creation of networks facilitates analysis via a simplified version of the Event Analysis of Systemic Teamwork (EAST) method. A strength of EAST is that it enables researchers to build a multiple network view of a research context (Walker et al. 2006). Research artefacts examined in the application of EAST enables the extraction of interdependencies, vulnerabilities and opportunities for response system optimisation. This research examined the social networks present in the case study and combined them with the task and knowledge networks developed using EAST to provide a ‘network of networks’ view of the problem (Salmon et al. 2014).
Approach
A total of 110 situation reports from Tropical Cyclone Winston, written by the National Disaster Management Office, were analysed in conjunction with CDM interviews (National Disaster Management Office 2016). The situation reports indicated the timeline of the disaster and the interviews indicated the elements of the identity management system. The timeline of the identity management system construction and implementation was extracted from this material and divided into ‘tasks’ using the EAST framework. Each task is represented in a joint social and information network to analyse the system’s effectiveness in recognising and addressing child trafficking and exploitation risks.
EAST method
The EAST method specifically analyses collaborative activities (Annett & Stanton 2000, Diaper & Stanton 2004, Birkmann et al. 2013, Vinchon, Carreño & Contreras-Mojica 2011, Walker et al. 2012). Identity management systems are characterised as being highly information and control dependent, where actors are dependent on the actions of others outside of their control to effectively mitigate risk (Lacey 2015). These environments are typically highly complex and collaborative; providing an appropriate basis for the research to adopt the EAST method. This approach is relevant to Cyclone Winston where actors did not remain the same.
Table 1 Participant information
|
Participant |
Age bracket (years) |
Gender |
Professional background |
Qualifications |
Years in position/ |
Organisation type |
Organisation size |
Role overview |
|
1 |
33-44 |
Female |
Over ten years’ experience working for IGO and NGOs globally |
Masters of Anthropology and Geography |
One year in current position |
NGO |
Large 1000 or greater |
Disaster response coordinator for large NGO |
|
2 |
55-64 |
Male |
22 years’ experience in the government sector and 15 years in the IGO sector working on gender and child related projects |
Over 30 years’ experience in government and non-government agencies |
Three months in current position |
NGO |
Large 1000 or greater |
Managing rural projects in the Cyclone Winston response |
|
3 |
NA |
Male |
Social worker and NGO worker |
Social worker |
One year in NGO |
NGO |
Small 100 or ess |
Child protection coordinator |
|
4 |
NA |
Female |
School teacher and NGO worker |
School teacher |
Less than five months in NGO |
NGO |
Small 100 or less |
Child program development |
|
5 |
NA |
Female |
Experience of over ten years in the NGO sector, experience over five years in the state sector |
University education and experience in the sector |
15 years |
NGO |
Small 100 or less |
Coordinator, CEO of national NGO |
Participants
For the purpose of this paper, ‘expert’ is defined as someone with experience in the DRE of Tropical Cyclone Winston. For fair perspective of the system, experts were from different organisations so information could be verified and compared to analyse the system’s reality, where data were put together to create the most realistic network possible. A small number of participants were interviewed for a rich qualitative dataset. A gender balance was sought for fair analysis of the system. Table 1 provides information about the participants.
Procedure
Initially, participants were interviewed using the CDM method. Once the interviews had been conducted and transcribed the data was analysed using EAST. The analysis used content analysis, taking keywords and concepts from situation reports and transcripts. The keywords and concepts were then connected to individual tasks. The identified relationships between tasks and actors created an output in the form of networks of information. In this study social network analysis is the key network portrayed.
Limitations
Limitations in data collection included the range of participants, where state actors were invited to participate but did not participate. The nature of the identity management system and shifting of identity responsibilities to non-state actors meant all participants actively engaged with state actors and provided detailed descriptions of roles and functions. There is a risk that limitations in interview data may create bias. To alleviate these risks, the data collection methodology included non-interview data to capture the actor perspectives (National Disaster Management Office 2016).
Results
The analysis indicates that the Fiji task network would look like Figure 1. This follows the top-down approach where the state is the lead actor. CDM interviews revealed that reality is more complex. The task network constructed from the case study represents how each actor is connected. This is achieved by combining the social and information networks in each task.
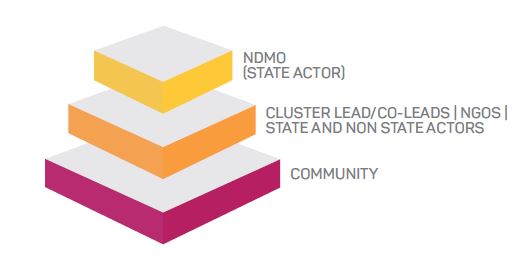
Figure 1: A traditional approach to the task network in identity management systems
The EAST analysis has been split into a timeline (Figure 2) with each task along the timeline represented in a network. The communication methods between actors included teleconferences, face-to-face meetings, email, phone calls, radio, television, word of mouth and SMS messages.
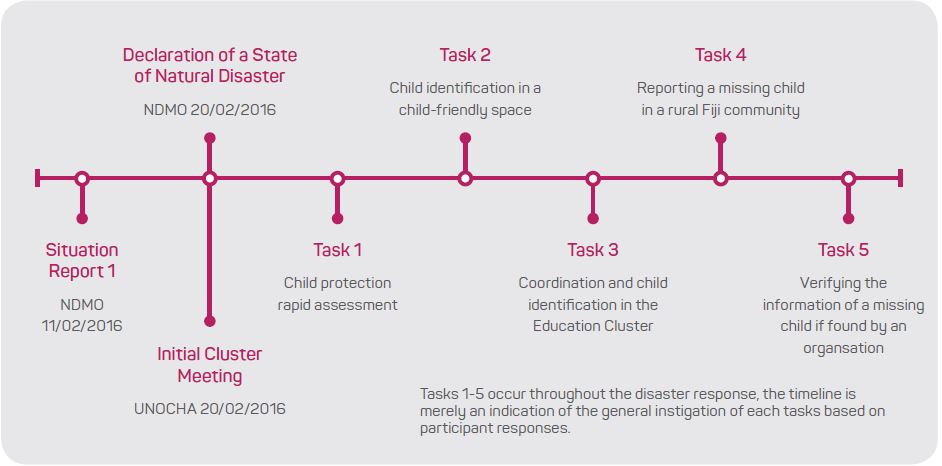
Figure 2: Progression of disaster response for Tropical Cyclone Winston
Task 1 (Figure 3) illustrates the social and information networks in the child protection rapid assessment. Each line represents information being shared between actors. A risk is present where NGO volunteers lack training and English fluency, thus increasing the risk of inaccurate information sharing. Risks occur when assessment is executed by one actor and shared. This procedure is based on trusting one actor solely for accurate and reliable information, thus increasing the potential for error.
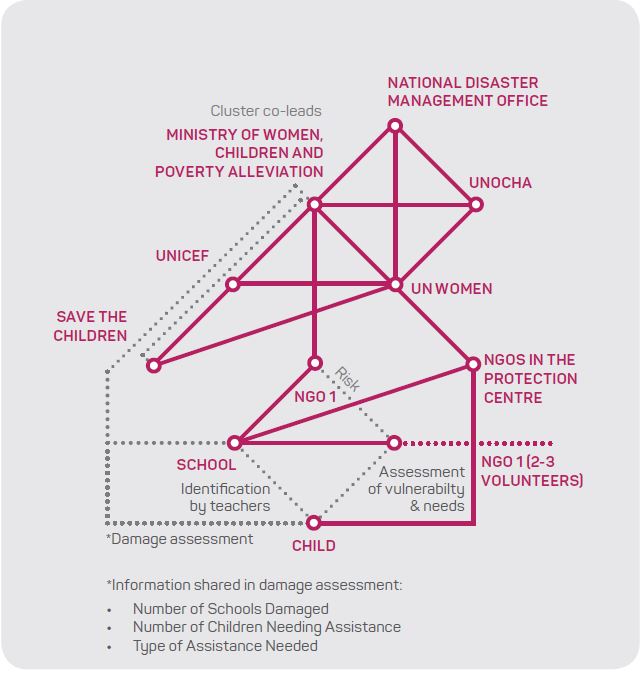
Figure 3: Task 1 - Child Protection Rapid Assessment
Task 2 (Figure 4) represents the identification process of a child within a child-friendly space in an evacuation centre. The red lines in the network represent a risk to the child where participants identified a lack of reliability of birth registration and enrolment data. The lack of information meant organisations were unaware of the exact number of children until they were in the DRE. The lack of birth registration and enrolment data indicates a risk where, if children were to go missing, formal identity processes could not be relied on. In this task, the reliance of knowledge-based authentication of identity is high and represents significant reliance on community-based identification processes.
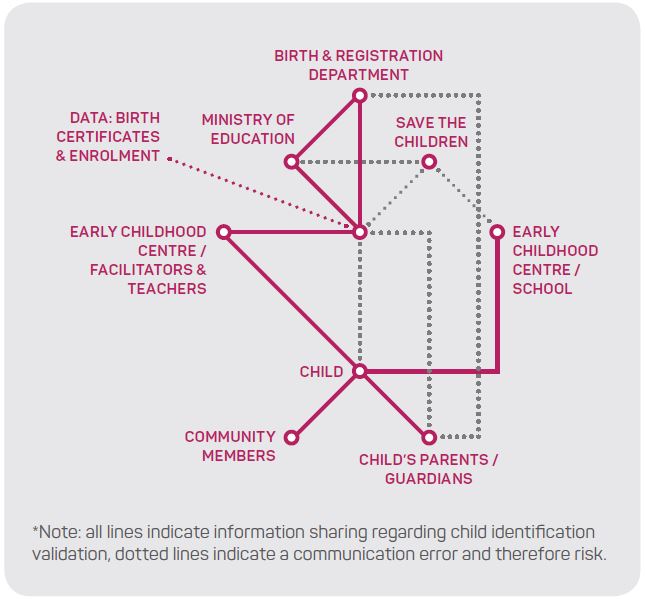
Figure 4: Task 2 - Identification in a child-friendly space.
Task 3 (Figure 5) represents the identity management system of children from the perspective of the Education Cluster. The more lines pointing at the child node, the higher risk, where more actors coming into contact with the child means less accountability of individual actor actions. For example non-registered organisations and individual ‘helpers’ are not connected with other actors and are not accountable to the government nor to other organisations and there is an inconsistency in identity management training. Additionally, for individual actors, their identities and qualifications are not always verified, nor do they follow the same child protection codes as those registered in the cluster. This represents a significant risk to children.
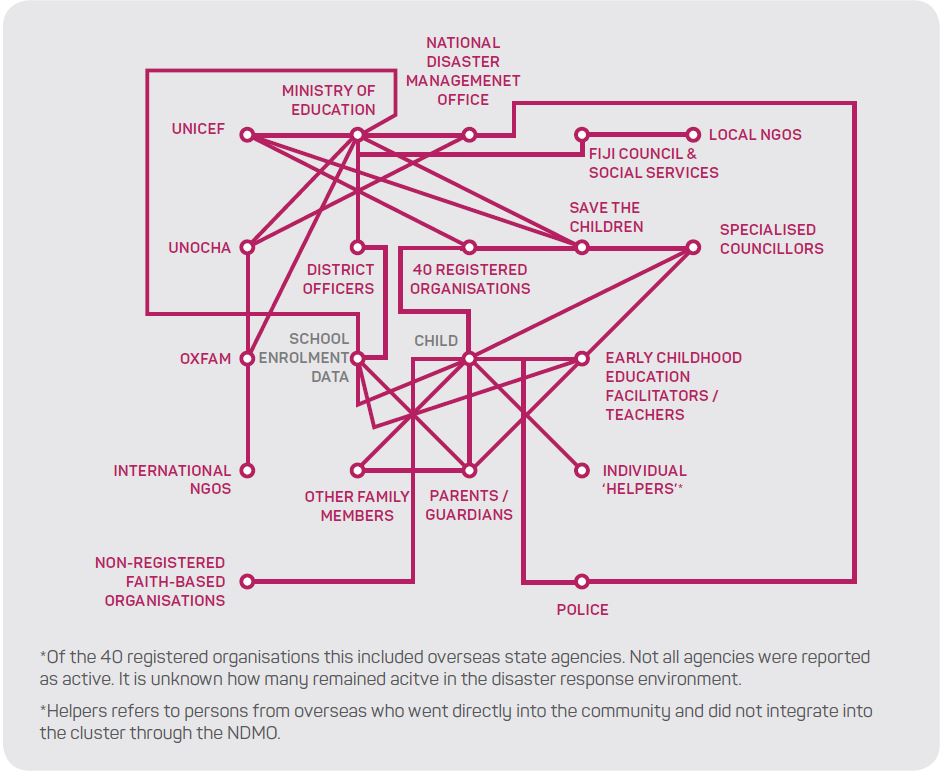
Figure 5: Coordination and child identification in the Education Cluster.
Task 4 (Figure 6) represents the reporting process of a missing child in a rural area in Fiji. This is significant because it highlights the importance of the community in the process where outside actors are not contacted until 24 hours after the initial report. This directly relates to Task 5 (Figure 7), where the identity management system relies on the child finding an organisation and the organisation reporting the missing child to the state. These tasks represent both sides of a situation of a missing child. However, the actors involved in the individual systems bear no resemblance to one another. Where Task 4 relies on the community to find the child, Task 5 relies on cluster-based actors to identify the child. As shown in Task 2, children are not always registered at birth or enrolled in education facilities but rely on knowledge-based identity authentication from the community for identity verification. Participants were unclear on what or how the identity of a missing child would be managed if the child had no formal documentation. CDM interviews raised a concern where the identity management systems need to be improved in non-DREs and DREs. Interviews revealed that there is a cultural barrier in understanding the need to formally enrol or register children.
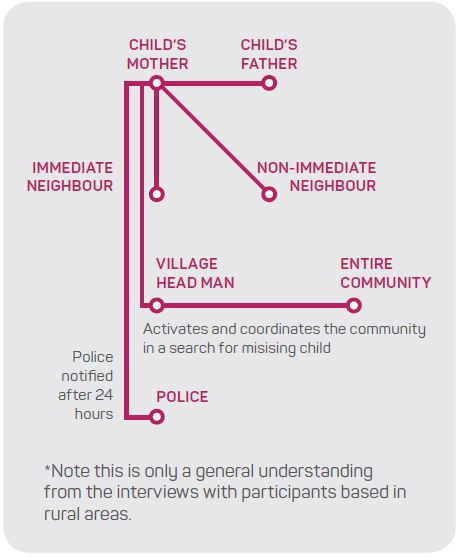
Figure 6: Task 4 - The Reporting of a missing child in a rural Fiji community (Koro Islands).
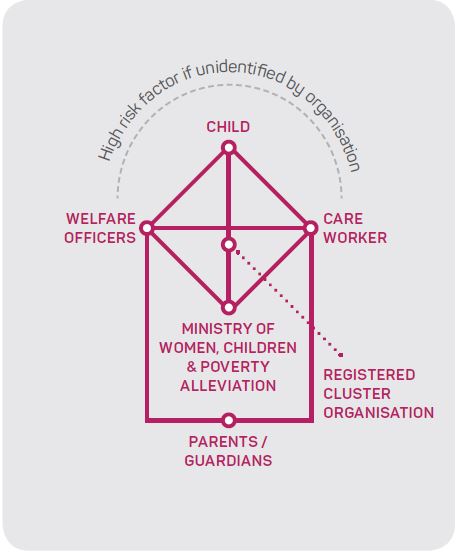
Figure 7: Task 5 - Verifying the information of a missing child if found by an organisation.
Interviews highlighted a risk to children when they are unidentified by an organisation and outside of the community environment. In the aftermath of the cyclone, some children left rural communities to attend school in urban areas. In these areas, the push factors for children to enter into exploitative work were higher. Push factors include financial to address basic needs such as living costs and food. When children move to urban areas their living situation is often unknown to those who provide protection to the child.
Discussion
This research shows there is a range of factors that affect coordination in a DRE. The nature of the identity management system in Tropical Cyclone Winston was based on knowledge-based authentication by the community in conjunction with official documents and data systems. Leaders in the community had a large role and teachers and early childhood centre facilitators were the frontrunners for identity verification, specifically in child-friendly spaces.
Identity management systems in DRE
The findings show that the risk to a child increases when there is a lack of identity management within a DRE, particularly when the child is separated from parents and the community. The networks indicate that the identity management systems of the community protect children using a grassroots, bottom-up approach. Interviews revealed that parents are the initial layer of protection, proceeding to neighbours and then the community with the state as the overarching actor in formal identity management systems. However, findings show that community-based informal identity management process provides the best risk-mitigation practice.
A key risk factor in traditional top-down identity management processes was data reliability and communication. The lack of reliability of formal identity meant it could not be 100 per cent effective. Community-based identity management, especially those formed by teachers, was the primary methods of identity management and protection
The risks of child trafficking and exploitation in the DRE in Fiji were not seen as high in this research. All participants stated this was due to the community-based culture of Fiji, where children are the community’s priority in a disaster. However, all participants stated that exploitation was present in Fijian society and that risks in a DRE were no higher than normal unless children were taken out of the community or were in evacuation centres. Participants emphasised that Cyclone Winston was unique to other disasters because most evacuation centres were in schools or early childhood centres. This meant that teachers had influence and responsibility in the child protection system. The teachers’ familiarity with children in their localities filled gaps in formal identity systems. NGOs relied on community grassroots levels of identity management, intertwined with the top-down system. This only works when information sharing is present and consistent across all actors; when communication breaks down so does the identity management and protection process.
Non-state actor experiences during Cyclone Winston
In this study, the overarching responsibility of identity management systems was the state. This was identified as a unique aspect of the Fijian disaster response. Participant 1 had significant experience in disaster response across three continents and stressed that the Fijian response was unlike that of other nations. For example, the child protection cluster was headed by the Department of Women, Children and Poverty Alleviation and co-led by Save the Children and UNICEF (Participant 3). This shows the top-down approach to policy implementation where the state remains the responsible actor. The two large Intra-Governmental Organisations (IGO) and NGOs as co-lead indicates the importance of non-state actors in the implementation of policy and systems.
The DRE of Cyclone Winston involved over 100 stakeholders with 42 organisations in the child protection cluster. Interviews revealed that state-led disaster response mechanisms were effective, however, the number of actors involved provided implementation challenges. Participants 2, 3 and 4 considered that duplication of response was a concern for organisations. Communication and implementation issues arose when stakeholders by-passed the cluster formation and proceeded with individual response plans. This lack of accountability to the state and processes meant organisations and individuals who worked separately exposed children to risks that are not easily tracked. Interviews revealed concern with reliability and quality of aid, specifically in psychological first aid provided to children by organisations and individuals outside the cluster system.
Conclusion
The DRE of Cyclone Winston was a complex environment with a multitude of state and non-state actors. The modified EAST method showed the identity management system was reliant on community actors, revealing that risks were escalated when children were taken out of the community. The EAST method provided a unique view of the dependencies between actors. Teachers, early childhood centre facilitators and village headmen played a key role in communicating and validating identification information. The lack of formal registration of children meant there were significant gaps in data for identity management. Limitations in the accurate recording of identity data meant that knowledge-based authentication was the primary verification method. Unaccompanied or separated children relied on welfare and case workers for family reunification. Interviews identified a high-risk factor for children who did not encounter an organisation, where data is lacking and that missing children are difficult to trace. Where an identity management system exists and verification mechanisms have geographical portability, risks to children are low. Further research is recommended into identity management systems and implementation where frameworks outside the community environment must be created to mitigate risks to children.


